 |
| https://www.tech-house.com/wp-content/uploads/2021/09/2021-09-Microchip-Blog-Image-1.png |
Microchips are tiny electronic devices that power everything from smartphones to computers to automobiles. They are made up of billions of transistors. These tiny electronic switches can be turned on or off to represent the ones and zeros of digital data. The more transistors a microchip has, the more powerful it is.
For decades, the size of transistors has been steadily shrinking, a trend known as Moore's Law. (Moore's Law, named after Intel co-founder Gordon Moore. He predicted in 1965 that the number of transistors on a microchip would double approximately every two years, leading to exponential improvements in the performance and efficiency of microchips. ) This has allowed the creation of increasingly powerful microchips that are smaller, faster, and more energy efficient. However, there is a physical limit to how tiny transistors can get, and we are approaching that limit with current technology.
 |
| The graph depicts Moore's law. https://www.tf.uni-kiel.de/matwis/amat/semitech_en/kap_5/backbone/r5_3_1.html |
One nanometer (nm) is one billionth of a meter. It is currently the smallest scale at which transistors can be reliably produced. While there have been efforts to push the limits of transistor size even smaller, such as using exotic materials like graphene, it has proven to be very difficult to produce functional transistors at the 1nm scale. So far, the smallest architecture we have achieved is 5nm, which tech giants like TSMC and Samsung recently announced.
There are several reasons why producing transistors at the 1nm scale is challenging. One is the challenge of creating and manipulating materials on a small scale. Another is the issue of quantum tunneling, in which electrons can "leak" through the barriers that are meant to contain them within a transistor. This can lead to transistors that are less reliable and require more power to operate.
Despite the challenges, tech giants like Intel, TSMC, and Samsung are among the companies that are actively researching and developing smaller transistor architectures. In recent news, TSMC has announced plans to start manufacturing 4nm chips by 2024 after completing their new manufacturing plant in Arizona. They are exploring various approaches, including the use of new materials and designs and ways to build multi-level microchips that can pack more transistors into a smaller area.
Apple, one of the world's leading technology companies, has also made strides in the microchip market with its M1 and M2 chips. The M1 chip, released in 2020, features a 5nm architecture and has received widespread acclaim for its performance and efficiency. The M2 chip, released on June 24, 2022, is made with TSMC's "Enhanced 5-nanometer technology" N5P process and contains 20 billion transistors, a 25% increase from the M1. Apple claims CPU improvements of up to 18% and GPU improvements of up to 35% compared to the M1. M2 is the second generation of ARM architecture intended for Apple's Mac computers after switching from Intel Core to Apple silicon, succeeding the M1.
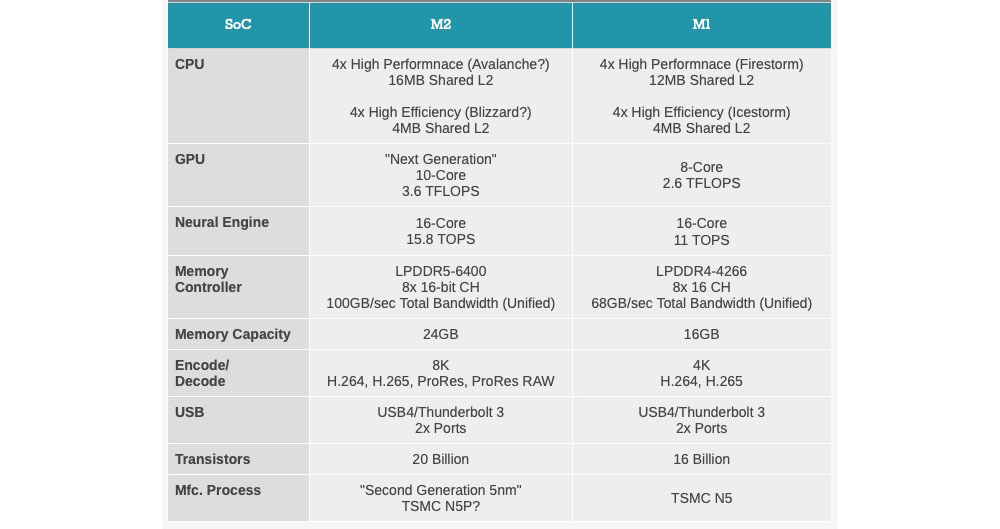 |
| Comparison of Apple M1 & M2 Chips https://9to5mac.com/2022/06/07/m1-versus-m2-chip/ |
In conclusion, while it may be technically possible to produce microchips with 1nm architecture, it is currently not feasible with current technology. So far, the smallest architecture we have achieved is 5nm, which tech giants like TSMC and Samsung recently announced. Companies like TSMC are already working on the next generation of smaller microchips. Apple is also pushing the boundaries with its M1 and M2 chips. However, that doesn't mean that the advancement of microchips has come to a halt. There are still many ways we can improve these important devices' performance and efficiency, even if we can only shrink them down a little further.


















